
What is Scrypt Algorithm & Top Scrypt Coins to Mine
Quick Summary
The Scrypt algorithm comes after the SHA-256 when talking about prominence and functioning. The Scrypt algorithm is mainly associated with Litecoin, a lighter version of Bitcoin(employing SHA-256).
This blog aims to provide a detailed insight into the Scrypt algorithm, its working, minable coins, advantages, and disadvantages for thorough understanding.
Scrypt Algorithm Explained
The cryptocurrency Litecoin was among the earliest to use Scrypt as a hash function instead of the more commonly utilized SHA-256 hash function. The mining algorithms employed by the Bitcoin and Litecoin protocols are Scrypt and SHA-256, respectively. Both function within the proof-of-work consensus method, in which a miner must discover a nonce value—a variable—so that the final result of a candidate block header hashing equals or falls short of the target value.
The target measures a miner’s difficulty in producing a valid block; the less the desired value, the more challenging it is to generate a valid block. On the other hand, a miner finds it more accessible to produce a legitimate block the higher the target value. Since Litecoin has a 2.5-minute block generation time, the target will modify itself in difficulty such that a miner can produce a successful block every 2.5 minutes.
Working of Scrypt Hash Function
A well-known technique for increasing key derivation through complex sequential memory functions is what makes Scrypt function. Scrypt hashes using a key, a set of critical points indicated in the hashing algorithm, and a lot of noise. Yes, it’s a complicated name.
Scrypt noise is a randomly generated sequence of randomly generated numbers kept in memory by the algorithm. These numbers mask the algorithm’s vital information, making cracking the hashes more difficult. Put simply, it is a security measure that keeps criminals from accessing data that Scrypt secures.
- First, the Scrypt hash function starts with hashing the password.
- The second step is to create cryptographic keys required to authenticate the data.
Features of Scrypt Algorithm
Below listed are some of the features that the Scrypt algorithm possesses:
- Since Scrypt was not intended to be accelerated by specialized mining hardware, it is challenging to use specialized hardware to compute Scrypt hashes more quickly. Therefore, it can be used in altcoins intended to resist ASICs. But throughout the time since the first ASIC for Scrypt was released in 2013, mining cryptocurrency based on Scrypt hash has been supported by ASIC miners.
- Since Scrypt is a memory-hard execution, computing a Scrypt hash requires significant memory. Because of this, performing Scrypt hashes is more costly than using other cryptographic hash functions like SHA-256.
- The output produced by Scrypt is variable-length, indicating that its length can change based on the input data. The Scrypt algorithm allows the output’s length to be specified as a parameter.
- Scrypt is utilized in many different applications, including encrypted transmission and password storage, as well as in the blockchain sector.
- Attackers are discouraged from attempting to recover user passwords from the saved hashes by using password algorithms for one-way processes, making it computationally impossible to deduce the initial login information from the hash output.
Compatibility of ASICs and Scrypt
The Litecoin developers first introduced the Scrypt hashing algorithm to prevent what is known as Application-Specific Integrated Circuits from being able to conduct mining on the Litecoin network. Users usually have three options when mining cryptocurrencies: CPU, GPU, or ASIC miner.
Because ASICs can produce more hashes per second than CPUs and GPUs, they are computationally more compelling to them. As a result, miners who mine for cryptocurrencies using any equipment other than an ASIC are at a disadvantage.
Since the Scrypt mining algorithm requires a lot of memory, it was designed to prevent ASIC mining. As a result, miners using CPUs and GPUs could maintain their competitiveness, while ASIC miners were initially ill-suited to mine on Scrypt-based mechanisms.
But as time passed, the Scrypt mining algorithm’s original “ASIC-resistance” vanished. It is now possible to mine cryptocurrencies that employ the Scrypt algorithm effectively due to the development of ASICs that are Scrypt-capable. Since ASICs have more computational power than CPUs or GPUs, these traditional mining tools are no longer suitable for the Litecoin network.
Advantages of Scrypt
Here are a few advantages of the Scrypt algorithm:
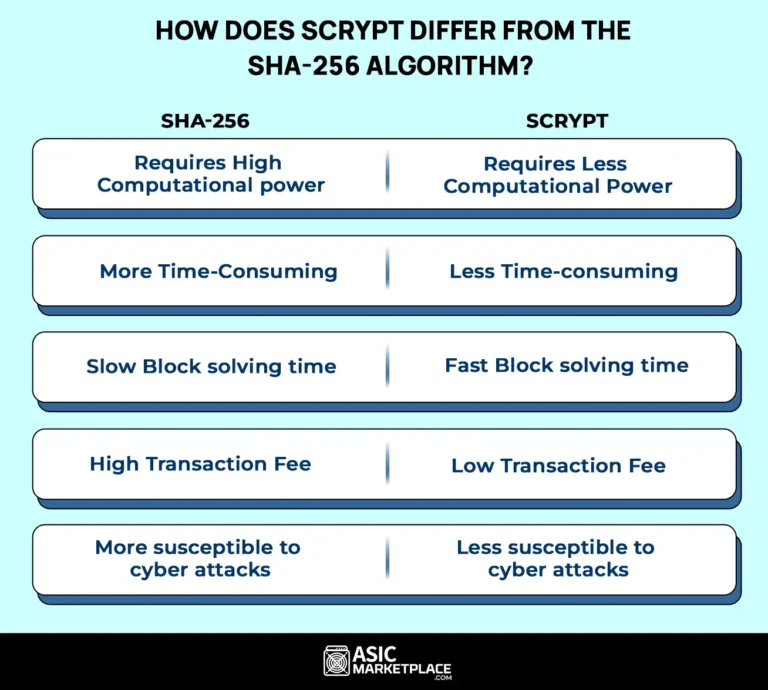
- Scrypt miners consume less time as the block-solving time compared to Bitcoin allows for four times faster block mining. Furthermore, SHA-256 mines in Terahashes, whose mining range is from Kilohashes to Megahashes per second, guarantee faster conversions.
- Scrypt uses fewer resources than SHA-256 regarding energy, equipment, and time. It makes Scrypt one of the best altcoin hashing algorithms.
- No security breach has been reported for Scrypt until now because it is computationally challenging to attack; the algorithm is secure and resistant to conventional attacks.
- Scrypt has a Less computational capacity, which is why it uses less energy. Because of its architecture, which prevents ASIC dominance, Scrypt typically consumes less energy than SHA-256, which is why most individual miners prefer it.
Disadvantages of Scrypt
There are not many disadvantages to using the Scrypt algorithm; however, let’s look at a few known limitations of the Scrypt algorithm:
- Scrypt’s high memory consumption is one of its main drawbacks, which can be problematic in settings with constrained resources.
- Its memory hardness also limits its usefulness in less powerful systems, even though it is a strength against some attacks because it requires more hardware for genuine use.
Top Scrypt coins to mine

How does Scrypt differ from the SHA-256 algorithm?
Check out the latest Scrypt Miners
Check NowConclusion
Several algorithms are competing with one another for market share. It is well-known that SHA-256 is the most widely used. However, other significant players serve the diverse crypto market.
An excellent example of this algorithm is Scrypt. Despite initially being designed for a different purpose, it has established itself in the cryptocurrency market. It has a lot of functionality despite its naturally light design. For users searching for a different offering and applications for encrypting files, wallets, and application passwords, the Scrypt algorithm is an ideal substitute.
FAQs on Scrypt Algorithm
-
Is Scrypt a secure algorithm?
Yes, Scrypt is a password-based hashing algorithm that is irreversible and secure in all ways.
-
Are Scrypt-employed coins still ASIC-resistant?
After the technological advancements, Scrypt brings better results with ASICs now than conventional mining equipment.
-
How much is mining one block required using the Scrypt algorithm?
It takes about 2.5 minutes to solve one block using the Scrypt algorithm.
Related Blogs

What is Scrypt Algorithm & Top Scrypt Coins to Mine
The Scrypt algorithm comes after the SHA-256 when talking about prominence and functioning. The Scrypt algorithm is mainly associated with Litecoin, a

Top Bitcoin Miners of 2024
The landscape of Bitcoin Mining keeps developing and adapting to the constantly shifting market. Miners’ utilization of Bitcoin mining hardware

What is The KHeavyHash Algorithm?
The KHeavyHash algorithm is emerging as a popular algorithm with time. The coin associated with it is Kaspa(KAS), which is
